The security of your data requires the existence of mechanisms on your network as well as on your individual devices. For this reason, we have entered into strategic partnerships with the best security providers and equipment manufacturers worldwide. We provide you with solutions that protect your infrastructure effectively at all levels. Ideally, you can combine this service with backup.
Network & Endpoint Security
OUR SERVICES
Network & Endpoint Security
- Central management console for all your machines and alerts
- Vulnerability assessment for each machine
- Data Loss Prevention to monitor and/or prevent the use of external storage media by users as well as the sending of data via web communication channels
Next-generation Firewalling
Endpoint Security
Email Security
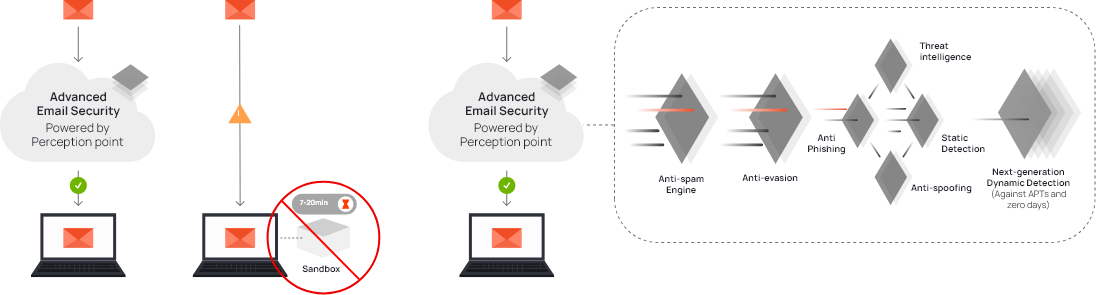
Regardless of whether you use MS365, Google Workspace or an in-house Exchange server, we can fully protect you through Perception Point’sinnovative solution. Using AI mechanisms and other parameters, any threat or malware that can be sent to you via Email is immediately recognized. This feature enables you to protect yourself against known threats such as phishing and spoofing. At the same time, it protects you against new threats for which your employees do not have time to be informed and trained in time. The solution complements the security mechanisms provided by Microsoft or Google in the case of cloud solutions. The mechanisms of the above Cloud Providers form a good basis but no business should consider itself completely protected by them.

“
Using a next-generation mechanism and multi-layer protection that reduces email checking time
from 20 minutes (sandbox) to less than 30 seconds.
OUR SERVICES
Services Features
- Next-generation firewalling
- IPS (real time & signature based)
- VPN Connections
- Antivirus, Anti-malware, anti-ransomware
- Zero-day threats protection
- Sandblast – AI (real-time Email & file scan)
- 7 layer protection
- Anti-malware scans to ensure malware-free backups
- Signature-based detection
- Exploit Prevention
- Forensic data in backups
- Remote device wipe in case an unauthorized individual tries to access one of your devices, e.g. laptop
You can find out more information at the following links:
